
Russian meddling in media space, efforts to undermine Europe’s cybersecurity
Russia’s main goal is to justify its war against Ukraine in the eyes of the Western audience and destabilize Europe, reads the report by the Center for Strategic Communication and Information Security.
Disinformation and propaganda
In a report on disinformation and manipulation of facts in the global information space in 2022, the European External Action Service named Russia the main misinformation actor of 2022.
The report stresses that Russia spreads fakes through official diplomatic channels, state media that broadcast to both Russian and foreign audiences, as well as through pro-Kremlin channels on the Internet that hide their direct ties with the Russian government, but can receive funding from Moscow. Among the most indicative examples of disinformation in the European Union were the media companies Sputnik and Russia Today (RT).
Read more about how Russia misinforms the world with the help of Russia Today in the study of the Center for Strategic Communication and Information Security “RT: Why Russian State Media Has no Place in the Civilized World”
According to the agency, the main topic of Russian information attacks was Russia’s war against Ukraine. In sixty cases out of one hundred, their goal was to justify the full-scale Russian invasion of Ukraine.
It is also important to note that the resolution “Legal and Human Rights Aspects of the Russian Federation’s Aggression against Ukraine,” adopted by the Parliamentary Assembly of the Council of Europe (PACE) on January 26, recognized the Russian official rhetoric used to justify the full-scale invasion and aggression against Ukraine as having signs of public incitement to genocide and may indicate a genocidal intention to destroy the Ukrainian national group as such or at least part of it.
Distribution channels, bots, and coordinated inauthentic behavior
To spread disinformation messages, Russia resorts to any means, including websites, social networks, and bot farms.
For example, in August 2022, NewsGuard discovered 250 sites that actively published Russian disinformation about the war, dozens of them were created after the full-scale Russian invasion of Ukraine. Some sites claim to be independent think tanks or news outlets. About a half are English-speaking, while others distribute materials in French, German, or Italian.
Many of them were also created long before the war and did not show their connection with the Russian government, until they suddenly began to spread Kremlin narratives. NewsGuard calls them “hibernating” sites. They gradually built up audiences by publishing neutral material, and then turned to propaganda or disinformation — when the Kremlin needed it.
In addition, Russia continues to distribute RT content to European audiences even after the imposition of sanctions and a ban on its broadcast in Europe.
According to a study by the Disinformation Situation Center (DSC), the content created by RT still reaches audiences in the EU.
For example, researchers found that some RT video content appeared on social media under a new brand and logo. In the case of some videos, the RT brand was simply removed from the video, and it was reposted on a new YouTube channel, which is not covered by the EU ban.
The results of another study, conducted by the Institute for Strategic Dialogue think tank and published in July 2022, also show the continued impact of RT on western audiences. Among the main ways identified during the analysis are alternative domains and subdomains for RT, mirror RT websites, copy-paste websites, and aggregator websites.
For example, researchers found 12 sites mostly in German or Spanish, which are an exact copy of either RT Deutsch or RT en Español. In addition, the IP addresses of these sites and Google Analytics IDs are directly linked to the pro-Kremlin broadcaster.
Researchers found several articles about Ukrainian refugees, printed by official RT websites. Then, through a Google search, they found sites that printed articles with the same headlines — there were about 66 identical materials in German, Spanish, English, and French.
According to the study, the Twitter account of RT en Español, which has millions of followers, invites people to visit a Spanish-speaking site that circumvents EU sanctions, and on Facebook, these sites appeared in over 1,200 open groups, which together have tens of millions of followers.
A similar situation is with the penetration of Russian propaganda among European audiences on social networks.
For example, recently, TikTok discovered a Russian disinformation network that spread military propaganda about Ukraine among more than one hundred thousand European users. The network operated in Russia, but was aimed mainly at residents of Germany, Italy, and the UK. About 1,700 accounts spread anti-Ukrainian messages, posing as local users. In this network, TikTok accounts used language synthesis and disseminated pro-Russian statements in the native languages of the targeted countries.
In September 2022, Meta also exposed a large network of Russian bots targeting primarily Germany, France, Italy, and the UK. It began operating in May and was centered around a network of 60 sites posing as real news media in Europe.
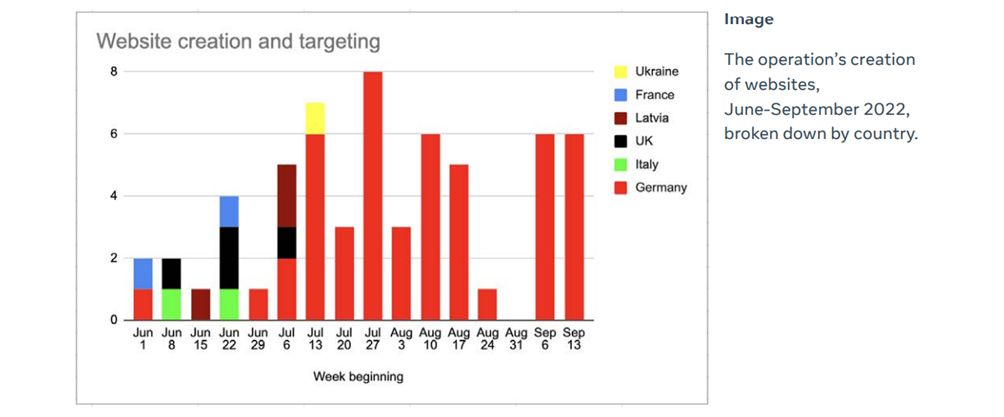
Source: Meta report “Taking down coordinated inauthentic behaviour from Russia and China”
Disinformation messages were created on fake sites and promoted on social platforms including Facebook, Instagram, Telegram, and Twitter. Bots were given the same names on several sites to create the illusion of the existence of such a person.
Information was disseminated in German, English, French, Italian, Spanish, Ukrainian, and Russian. Russian embassies in different countries reposted some of such accounts.
Earlier in May 2021, Meta published a report for 2017-2020 with an analysis of 150 information operations that were detected on Facebook. According to the results of the study, Russia was the largest supplier of disinformation. In four years, Meta has identified 27 influence operations. Of these, 15 were affiliated with the St. Petersburg-based Internet Research Agency (IRA) or other entities affiliated with Yevgeny Prigozhin, a Russian oligarch with close ties to Russian President Vladimir Putin. Four more Russian networks were linked to Kremlin intelligence services, and two more were linked to Russian media sites.
Russian hackers and cyberattacks
Media space is not the only goal of Russia, in addition, it also undermines Europe’s cybersecurity.
According to a Microsoft report, Russian hackers are engaged in “strategic espionage” against governments, think tanks, businesses, and aid groups belonging to Ukraine’s allies. Microsoft has detected attempts of Russian cyber intrusion in 128 organizations in 42 countries.
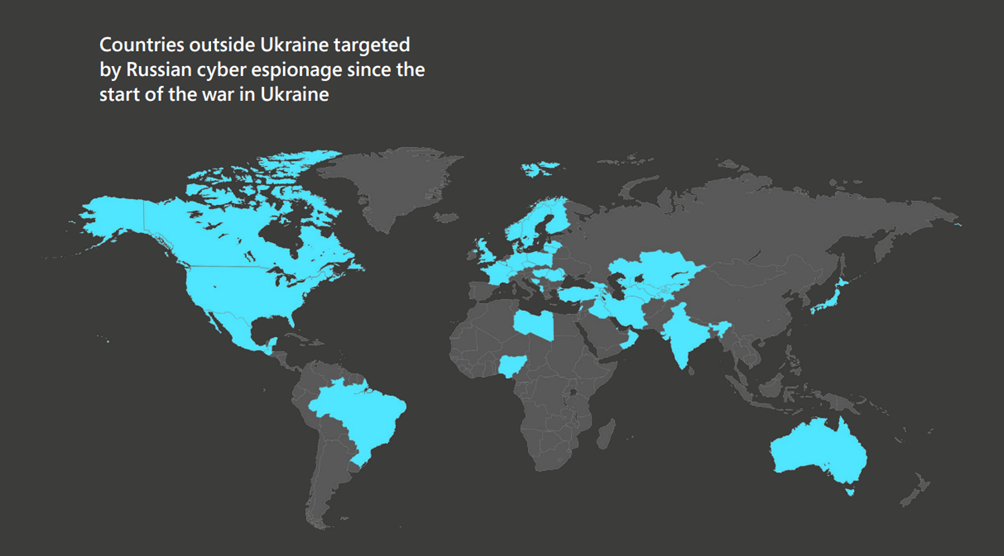
Source: Microsoft report “Defending Ukraine: Early Lessons from the Cyber War”
The United States was the main target, and Poland, which is the main channel of military assistance to the Ukrainians, was second. Denmark, Norway, Turkey, as well as Finland and Sweden, which have just applied for NATO membership, have also suffered significant attacks. Half of the 128 organizations affected are government agencies, and 12% are non-governmental organizations, usually think tanks or humanitarian groups. Other targets include telecommunications, energy, and defense companies.
In general, all attacks by Russian hackers on Ukraine’s allies since the beginning of the war have been successful in 29% of cases. Of these, only in a quarter of cases, the intervention led to data loss.
Google’s report on the changing landscape of cyber threats as a result of the Russian war against Ukraine states that last year, the enemy increased cyberattacks on Ukrainians by 250% compared to 2020. At the same time, the number of cyberattacks on users in NATO countries over the same period increased by more than 300%.

The pretexts for Russian cyberattacks are any manifestations of Western partners’ aid to Ukraine. One recent example — after the decision of the German government in January to provide Ukraine with Leopard tanks, hackers from the Russian group Killnet attacked the sites of several state institutions of Germany.
Therefore, Russia has launched a powerful information war against Ukraine and its allies, undermining the information security and cybersecurity of Europe. Such actions only confirm the illegality and criminality of Russia’s intentions towards Ukraine and its partners.
Center for Strategic Communication and Information Security




